1. XSS in Aliexpress
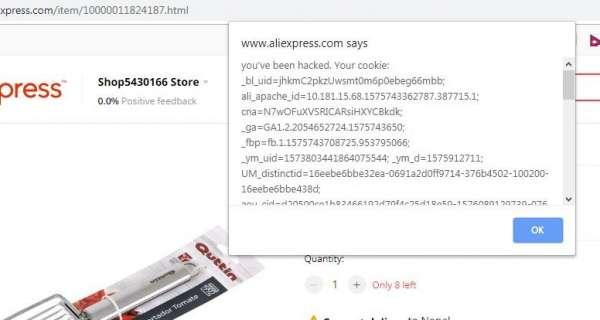
Aliexpress, Chinese website which worth billions had these vulnerabilites. I could insert javascript in their website and steal cookie from users, download malicious file, run malicious code, insert ads, redirect user to my website and many more.
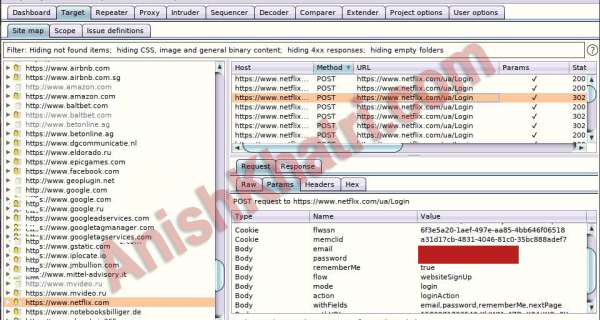
How did I do it?
well the add product on seller portal user rich text editor which then converts into HTML and send it to the server. I just intercepted it and added XXS in the script. Check the video below,
NOTE: I used onmouseover to trigger the XSS but I could have used onerror with img for better effect. and no user interaction would be needed to trigger the XSS
3. XSS in Alibaba
Alibaba has message center. Where users could message each other. The message didn't have HTML filter. Which means I could send html tags. But it was limited because whole Alibaba has a filter which prevents, XSS.
I could only send tags like <b>, <i> etc
and If I tried to send <b onclick="alert('xss')"> it wouldn't work because of the filter. So what I did was I used 'HTML decimal character reference' which bypassed the filter.
So I sent message like
<b onclick="alert('XSS')">Click here
this is html decimal reference for
<b onclick="alert(document.cookie)">
And it worked...
4. Summary
I reported it to Alibaba security team and they have fixed this. But other websites migh contain such vulnerabilites. Keep exploring but don't be evil...
5. Report Timeline
2019-Nov-18: Vulnerability found and reported
2019-Nov-19: First response from team
2019-Nov-21: Report triaged $1160 bounty rewarded
2019-Dec-22: $1125 transferred to my account Via Swift Transfer
This is just for information and might help other white hats to know better how their report get processed.